PROTECTION & SECURITYWe take the protection of the data held on the entityOS.cloud service very seriously. Protecting it from both internal and external threats. Security has to be seen as a "whole" - we use a number of core philosophies (in no particular order):
"Do you have a reason to know" This is all about layering and "Law of Demeter" - so the technical and human resources only need to know about their layer and protecting it with clear entry and exit interfaces. This aligns with the model-view-controller architecture. In the case of entityOS it is the fully hosted model - in that it has a single purpose to keep the data persistent and protected. Humans are a key weakness in any security system - we run the minimum required to have access to sensitive information.
Again using SoC principles - we use Amazon Web Services and leverage their investment in creating a robust and secure infrastructure layer.
In the case of entityOS that means one protocol only, being http. It then only has to look for entry based on one protocol and through two ports (80/443). With all traffic encyrypted using 256/2048 bit SSL.
The architecture of the application technology stack is key to being able to protect it. In the case of entityOS the UI/VC ("user mode") is separated from the Model ("kernel mode") - allowing for different security regimes based on the zone. Script injection is then controlled in the UI as the model always delivers up encoded data. Each layer is responsible for validating traffic as it enters and exits.
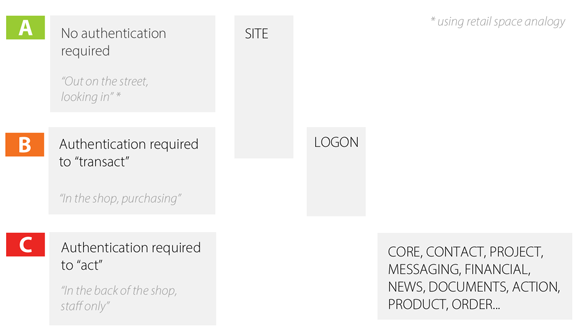
This allows each space owner to set up the security access at both a functional and data level. In the case of functional security, each method can be specifically pre-set based on in-model user roles. So no matter what view-controller is sending the http request, it won't get compromised. This control includes 2nd factor authentication.
We are constantly working with partners and trying to break our own system - more on testing ...
Security is a whole of community issue and we offer rewards to anyone that contributes to making the entityOS community safer. |
|||
 |
|||
|
ibCom uses the following to resources to guide its secure software development: |
|||
|
OTHER LINKS: |